Wireless LAN (SSID, ESSID, ANY connection, stealth function)
Wireless LAN (SSID/ESSID)
IEEE 802.11 series wireless LANs use identifiers called SSIDs to identify access points (wireless bridges, wireless broadband routers, etc.). This identifier can be any alphanumeric string up to 32 characters.
ESSID is an extension of the network identifier so that it can be used in networks with multiple access points, and the word SSID is now used to mean ESSID.
The SSID is set for the access point and the terminal, so that communication can only be performed with terminals that match the SSID.
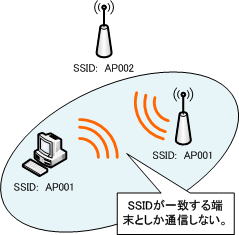
Since it is possible to restrict access by SSID, there was a time when it was regarded as one of the security functions of wireless LAN, but now it is not a function that can be called a security function.
If you set the SSID on the wireless client side to “ANY”, which allows connection to any access point, or “blank”, communication becomes possible. In addition, many access points transmit frames called “beacons”, which are signals that inform all wireless clients of the SSID.
This frame contains the SSID.
Therefore, you can communicate without setting the SSID.
Therefore, depending on the product, some wireless access points have a function that rejects connections from terminals set to “ANY” in consideration of security, and a stealth function that stops the beacon signal that informs the surroundings of its own SSID. I have some products.
The stealth function, which hides the SSID, can be used to hide the access point and increase security.
Wireless LAN (ANY connection, stealth function)
Many wireless broadband routers allow ANY connections by default.
Some older wireless broadband routers do not have a function to reject ANY connections. In that case, ANY connections are always allowed.
Allowing ANY connections greatly simplifies configuration on the wireless client side. Simply select it from the list and you will be able to connect to the wireless network.
In other words, allowing ANY connection allows anyone to easily connect to the access point. However, in terms of security, it becomes a very uneasy material.
Conversely, denying ANY connections improves security, but complicates the configuration of wireless clients and sacrifices operational aspects. If you allow ANY connection, a list of available access points will be displayed.
For example, if “AP001_G” is set for the SSID, “AP001_G” will be displayed in the list. You can connect just by clicking the displayed “AP001_G”.
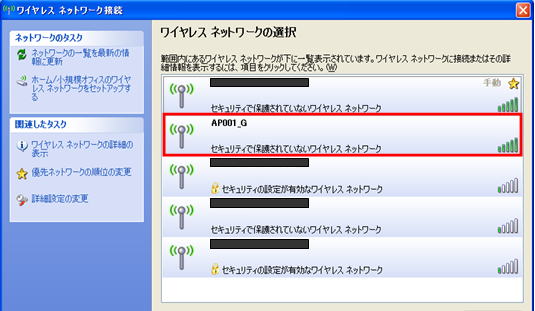
Permitting ANY connection in this way makes the settings on the wireless client side very simple and makes operation easier. You can connect to the wireless network simply by selecting it from the list without setting the wireless client.
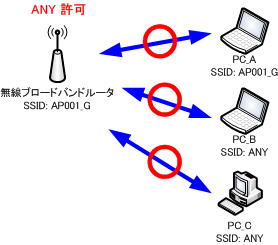
Allowing ANY connection allows anyone to easily access the access point. However, as it stands, I’m very worried about security.
Therefore, wireless devices such as wireless broadband routers have a function to reject ANY connection. Some products call it a stealth function.
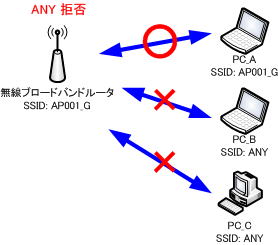
Denying ANY connections improves security and may seem like an effective measure at first glance, but it complicates the settings on the wireless client side and sacrifices operational aspects.
It complicates the configuration on the wireless client side. Wireless setup is complicated. There is also a lot of specialized terminology. If you don’t know much about networking, setting it up can be a difficult task.
As a result, not only will the number of inquiries to the network administrator increase, but depending on the situation, you may be called and set up each time, saying, “I can’t connect, please set up!”
If you want to increase security even if you sacrifice the operational side to some extent, setting to deny ANY connection is an effective means. In that case, it is necessary to create a connection procedure manual, disseminate it within the company, share it, and provide education.
It will not be displayed in the list if ANY connection is set to be rejected.
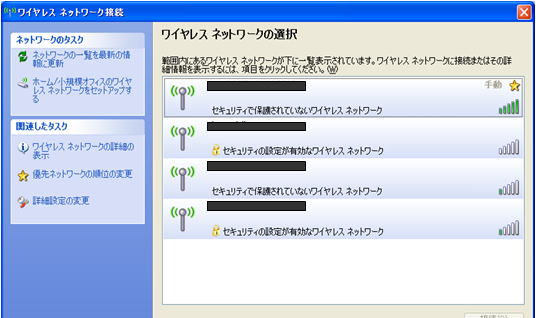
Instead, the wireless client must be configured with the SSID, network authentication method, data encryption, etc. to connect to the access point.