サイト間VPN(その6)
「サイト間VPN(その5)」の続きです。
ここでは、PC_Aから実際にPC_Bに通信が行えるかどうかを確認します。また、Router_AとRouter_Bのコンフィグを紹介します。
※サイト間VPNは、IOSが対応していなければ、設定することはできません。
ネットワークの構成は、以下の通りです。
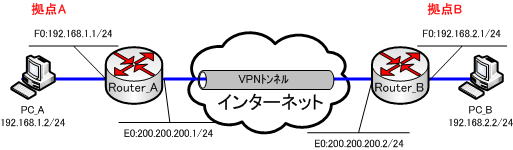
インターネットVPNの疎通確認
PC_AからPC_Bにpingを行います。
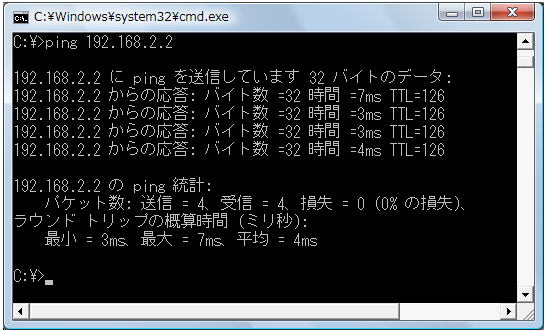
VPNトンネルが開通していますので、もちろんpingは成功します。
ルータの設定
●Router_Aの設定
!
version 12.4
service config
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router_A
!
boot-start-marker
boot-end-marker
!
no aaa new-model
memory-size iomem 25
!
ip cef
!
crypto pki trustpoint TP-self-signed-2739943660
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2739943660
revocation-check none
rsakeypair TP-self-signed-2739943660
!
crypto pki certificate chain TP-self-signed-2739943660
certificate self-signed 01
30820240 308201A9 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32373339 39343336 3630301E 170D3032 30333031 30383333
31335A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 37333939
34333636 3030819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100B801 2715B5BD 2CCA418A BCB72107 891716CF 99758697 A395941B CD3EE6C7
7339F674 37CF5F84 E3E13E2E CA3AEF16 07569309 CAA7AF3B D0CE1ADF EF4C14F0
18508FA3 F4EF215D 9F88C401 B4E67190 A15A9B1A 20FA9A11 97F1C4CC 650D79CD
2C797FCD 7993CDDD 3CBB89CB DF935B57 7FF5BB29 19B5B957 8F95C7B0 39F24690
23F10203 010001A3 68306630 0F060355 1D130101 FF040530 030101FF 30130603
551D1104 0C300A82 08526F75 7465725F 41301F06 03551D23 04183016 8014D679
AB085017 C0B1E2FD A6AE9B37 E1D3687E B6F7301D 0603551D 0E041604 14D679AB
085017C0 B1E2FDA6 AE9B37E1 D3687EB6 F7300D06 092A8648 86F70D01 01040500
03818100 6EB53D7A 1B983579 1A289726 56302905 75F73681 B6D72E46 745C79D3
6D2536F8 4F75E139 08FA71EC 7F3643A5 6565E05C 7379025B 72DFAA14 E37D8E30
00D2E98F 3861462B 9C98217D 2C7F3303 E0EDC747 6E73B6EF 95C43BFD 172802C6
EE636A95 E2E832B2 B8EFDE56 1258B890 71B786AA EA208436 B27475E1 D7756B0D BDC9591E
quit
username ccnaccnp privilege 15 secret 5 ccnaccnp
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 200.200.200.2
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto map SDM_CMAP_1 1 ipsec-isakmp
description Tunnel to200.200.200.2
set peer 200.200.200.2
set transform-set ESP-3DES-SHA
match address 100
!
interface Ethernet0
ip address 200.200.200.1 255.255.255.0
half-duplex
crypto map SDM_CMAP_1
!
interface FastEthernet0
ip address 192.168.1.1 255.255.255.0
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 Ethernet0
ip http server
ip http authentication local
ip http secure-server
!
access-list 100 remark SDM_ACL Category=4
access-list 100 remark IPSec Rule
access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
!
control-plane
!
line con 0
line aux 0
line vty 0 4
privilege level 15
login local
transport input telnet
!
end
●Router_Bの設定
!
version 12.4
service config
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router_B
!
boot-start-marker
boot-end-marker
!
no aaa new-model
memory-size iomem 25
!
ip cef
!
crypto pki trustpoint TP-self-signed-3359589021
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3359589021
revocation-check none
rsakeypair TP-self-signed-3359589021
!
crypto pki certificate chain TP-self-signed-3359589021
certificate self-signed 01
30820240 308201A9 A0030201 02020101 300D0609 2A864886 F70D0101 04050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 33333539 35383930 3231301E 170D3032 30333031 31303439
34365A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D33 33353935
38393032 3130819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281
8100C05C DD30F2D1 FB0B2CBE 3F3E8801 72096EE4 118884D8 756EFE27 8B388773
2D96665C B21040AE 05EAF5D0 42A1B05A 5D6775C3 E92268EA 5B7DD0A4 7C462F86
EBDB0FB7 D85EDCF1 D6B8DDF7 0EF790F5 9D8D1223 55CAD340 813D06F9 3626966E
69B70FB5 1A26A080 1C73292F A426141C 52F0FD71 9EFAB6B6 131246A3 4F27DF8F
3EB90203 010001A3 68306630 0F060355 1D130101 FF040530 030101FF 30130603
551D1104 0C300A82 08526F75 7465725F 42301F06 03551D23 04183016 8014C6B4
A0A05E08 08BEAC7A CF5C1DA4 DFE40545 CB55301D 0603551D 0E041604 14C6B4A0
A05E0808 BEAC7ACF 5C1DA4DF E40545CB 55300D06 092A8648 86F70D01 01040500
03818100 2E512703 5AD1983C B2670054 56697879 75F7C950 6E50B561 D237FC1A
1ECD4514 56924852 1E23B66A A8F0DCDD B0F1D314 1636FC0C 687B0E2F 5E7CDB24
919B8980 78423727 5C910439 58C01752 AAB35345 F05483E0 BA3D6ADA 44CFCEAC
95C4B1A5 74760F4A 1491567D 1AEEF5DF DA6DEB37 20ABB800 8AEB3943 1557BA19 EBE592DD
quit
username ccnaccnp privilege 15 secret 5 ccnaccnp
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 200.200.200.1
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto map SDM_CMAP_1 1 ipsec-isakmp
description Tunnel to200.200.200.1
set peer 200.200.200.1
set transform-set ESP-3DES-SHA
match address 100
!
interface Ethernet0
ip address 200.200.200.2 255.255.255.0
half-duplex
crypto map SDM_CMAP_1
!
interface FastEthernet0
ip address 192.168.2.1 255.255.255.0
speed auto
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 Ethernet0
ip http server
ip http authentication local
ip http secure-server
!
access-list 100 remark SDM_ACL Category=4
access-list 100 remark IPSec Rule
access-list 100 permit ip 192.168.2.0 0.0.0.255 192.168.1.0 0.0.0.255
!
control-plane
!
line con 0
line aux 0
line vty 0 4
privilege level 15
login local
transport input telnet
!
end
次の「サイト間VPN(その7)」では、設定したVPNを検証していきます。
