What is Static Filtering
What is static filtering
Static filtering statically creates conditions based on the following information and “passes” or “blocks” packets based on those conditions.
- source IP address
- Destination IP address
- Protocol type (TCP, UDP, ICMP, etc.)
- source port number
- destination port number
- direction in which packets flow
A set of conditions that determine whether to “pass” or “block” a packet is called a filtering table.
For example, let’s look at the contents of the filtering table when a firewall that performs static filtering is placed between the PC on the LAN side and the web server.
Register the packet forwarding and returning conditions in the filtering table so that only the packets that access the web server are passed.
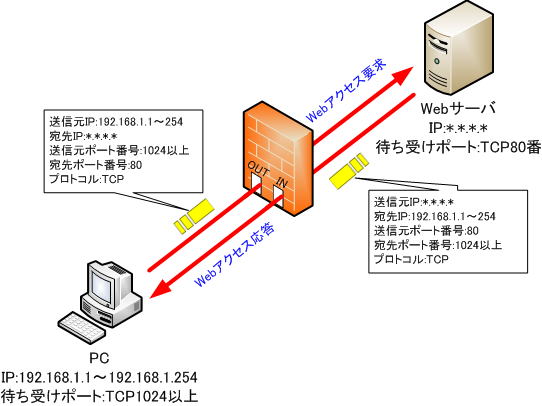
● Filtering table
| number | direction | protocol | source IP address | Destination IP address | source port number | destination port number | process |
| ① | → (inside → outside) | TCP | 192.168.1.* | *.*.*.* | * | 80 | passage |
| ② | ← (outside → inside) | TCP | * | 192.168.1.* | 80 | * | passage |
| ③ | * | * | * | * | * | * | cut off |
Filtering table rules
The filtering table has the following rules:
・The filtering table is inspected in order from the conditions on the table, and if the conditions are not met, the next condition is inspected.
・If the conditions are met, the inspection ends when the conditions are met, and the conditions after that are not inspected.
・”*” on the filtering table means all values that the item can take.
Now, I will explain the details of each condition from number ①.
● Number ①
The HTTP protocol is used to access the Web server, and TCP is used as the transport layer protocol. Web servers generally wait for Web access on TCP port number 80, so filtering is performed in the direction from LAN to Web server.
In the condition of number 1, it is specified to pass packets addressed to the web server from the PC whose source is the IP address on the LAN side.
● Number ②
Filtering is performed on the return packets from the web server to the PC on the LAN side. The source is the web server, and it is set to pass packets addressed to the PC on the LAN side.
● Number ③
All items have “*”. Blocks communication from all sources to all destinations. Under this condition, all communications meet this condition and are blocked.
Communication between the PC on the LAN side and the Web server is allowed to pass under the conditions of numbers (1) and (2), and all communication other than the Web meets condition (3), so HTTP communication between the PC on the LAN side and the Web server. only pass through the firewall.
Filtering direction and filtering conditions
In the firewall, you dictate which conditions apply to which interface in which direction.
There are also products that individually set whether the interface is outward (OUT) or inward (IN) for each condition. There are also products that will be applied to either (OUT) or inward (IN).
When considering packet filtering conditions, there is a policy that must be decided first. You must choose one of the two below.
(1) Specify only the packets to be blocked as conditions, and allow communication that does not match the conditions to pass.
(2) Specify only the packets to pass as conditions, and block communication that does not match the conditions.
Both may seem similar, but there is a big difference in security strength.
When specifying only the packets to be blocked as a condition and allowing communication that does not match the conditions to pass
This method defines possible attacks in advance as filtering conditions. All packets that do not match the conditions will be passed. There are countless dangerous attack methods, so it is difficult to define all without omission.
If there is an omission in the filtering conditions, unauthorized packets will enter. Therefore, it is necessary to review the firewall conditions from time to time to check whether there are omissions in the filtering conditions and whether new attack methods are being addressed.
When specifying only the packets to pass as conditions and blocking communication that does not match the conditions
This method pre-defines the packets you want to pass. All undefined communications are blocked, so you can ensure more security than method (1). Even if there is an omission of the definition, it will be blocked, so it is safe.
For the above reasons, the default filtering policy of many firewall products is to block all unmatched communications.
For example, Cisco routers have an implicit “deny any” access list at the end of the access list that defines the filtering rules by default, even if it is not defined.
In other words, since the default policy is to block, if there is an omission in the conditions to pass, it will be blocked.
Weaknesses of static filtering
Some applications use a large number of port numbers, creating too many conditions (holes) for packets to pass through, which can greatly reduce security.
Since there is always a hole through which incoming and outgoing packets can pass, the weak point is that there remains a risk of intrusion from crackers, viruses, etc.