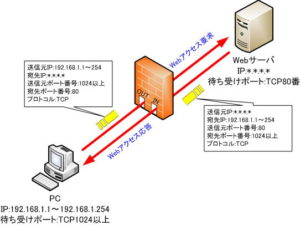
Limitation of TCP header specification for static filtering
Static filtering (specifying TCP headers)
Static filtering always leaves a hole for incoming and outgoing packets for the traffic you want to pass. Therefore, there remains a risk of intrusion from crackers, viruses, etc.
For example, if a hole is opened to pass the TCP port number 80 of the source for return packets to pass web communication, a cracker can disguise the source port and send a malicious packet , the firewall lets it through as a legitimate packet.
To block malformed packets like this, we can add a little more granularity to the firewall so that it looks at the information in the TCP header.
Communication in TCP
Before explaining how to specify TCP headers in firewalls, let’s first understand communication in TCP.
In TCP communication, a connection is established by a procedure called three-way handshake.
In this handshake, the two hosts synchronize their initial sequence numbers by exchanging initial sequence numbers.
Synchronization is done by exchanging packets consisting of a SYN (synchronization control bit) and an initial sequence number.
The steps are as follows:
| procedure | content |
| Step 1 | The sender sends a “SYN packet” to the other party. |
| Step 2 | The other party that receives the SYN packet sends a “SYN, ACK packet” to allow the connection to the sender. |
| Step 3 | The sender that receives the SYN ACK packet sends an ACK packet indicating connection initiation and initiates communication with the receiver. |
A diagram of the three-way handshake is shown below.
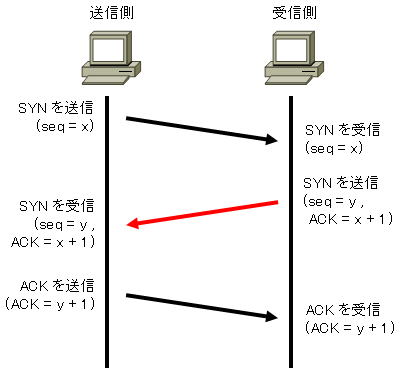
In this way, the three-way handshake establishes a connection by sending three packets back and forth.
The above diagram only shows the exchange of three packets, but the following packets will all be sent with the ACK flag turned on.
In other words, in TCP communication, the sending side sends a packet with the SYN flag turned on to the receiving side, and all subsequent packets turn on the ACK flag, which is an acknowledgment. I will send the packet.
Checking code bits in firewalls
A TCP header is constructed as follows:
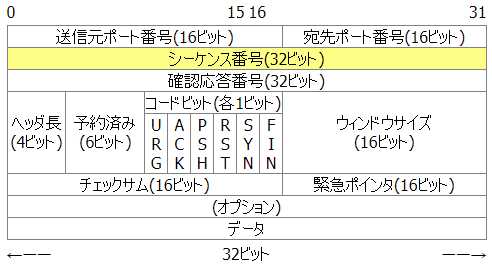
If the firewall checks whether the ACK in the code bit in the TCP header of the packet sent from the outside is turned on and allows only the packets with the ACK turned on, it will prevent illegal packets from the outside. can be blocked.
Communication in TCP is a procedure called three-way handshake, and communication cannot be performed unless a connection is established. By blocking packets with SYN turned on, the three-way handshake cannot be established and the TCP connection is established. no longer.
TCP allows fine-grained specification of static filtering by confirming the exchange of three-way handshakes in this way, but for UDP connections, there are no code bits in the UDP header, so TCP It is not possible to make detailed specifications.
This is the limit of static filtering.
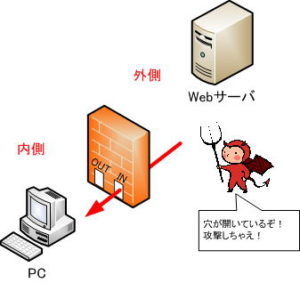
Limitations of static filtering
With static filtering, there is always a hole that allows incoming and outgoing packets to pass through, so there is a risk of intrusion from crackers, viruses, etc.
Some applications use a large number of port numbers, which can create too many conditions (holes) for packets to pass through, greatly reducing security.
There is always a hole that allows incoming and outgoing packets to pass through, making it easy prey for crackers and viruses to infiltrate.
Say goodbye to viruses and spamware
Packet filtering checks only a portion of the IP and TCP headers of passing packets to determine whether or not to allow them to pass. Therefore, if a virus or spamware is embedded in the data portion of a packet, it will bypass packet filtering.
Using a familiar example, if a file with a virus is attached to an e-mail attachment, it can be easily invaded.

So packet filtering is a no-brainer for viruses and spamware.
The only way to combat these attacks is to look inside the data in the packet.
However, since there are countless viruses and spamware, even if the firewall can check the data of passing packets, checking all packets for the characteristics of all viruses and spamware will cause a heavy load. It takes time and is not realistic.
Therefore, it is necessary to deal with these viruses and spamware by using a personal firewall that is directly installed and used on personal computers.
Poor intrusion detection and attacks
It is vulnerable to buffer overflow attacks that bring down servers and DoS and DDoS attacks that overload servers and network equipment.
In order to detect and prevent unauthorized access that cannot be prevented by such filtering, it is necessary to combine with devices such as IDS and IPS.