VPN(GREトンネルとルーティングプロトコル 3)
「VPN(GREトンネルとルーティングプロトコル 2)」では、IPSec 上にGREトンネルを設定しOSPFでルーティング可能にする設定を紹介しました。ここでは、各ルータのコンフィグを紹介します。
Router_BのE0は、「no keepalive」し、強制的にUPさせます。
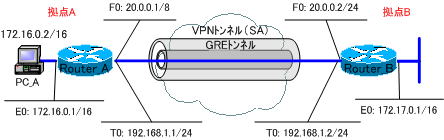
各ルータの設定は次のようになります。
●Router_Aの設定
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router_A
!
boot-start-marker
boot-end-marker
!
enable password cisco
!
no aaa new-model
memory-size iomem 25
!
ip cef
!
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 20.0.0.2
!
crypto ipsec transform-set TS-IPSEC esp-3des esp-sha-hmac
!
crypto map MAP-IPSEC 1 ipsec-isakmp
set peer 20.0.0.2
set transform-set TS-IPSEC
match address 100
!
interface Tunnel0
ip address 192.168.1.1 255.255.255.0
tunnel source 20.0.0.1
tunnel destination 20.0.0.2
crypto map MAP-IPSEC
!
interface Ethernet0
ip address 172.16.0.1 255.255.0.0
half-duplex
!
interface FastEthernet0
ip address 20.0.0.1 255.0.0.0
speed auto
crypto map MAP-IPSEC
!
router ospf 1
log-adjacency-changes
network 172.16.0.0 0.0.255.255 area 0
network 192.168.1.0 0.0.0.255 area 0
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
access-list 100 permit gre host 20.0.0.1 host 20.0.0.2
!
control-plane
!
line con 0
line aux 0
line vty 0 4
password cisco
login
!
end
●Router_Bの設定
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router_B
!
boot-start-marker
boot-end-marker
!
enable password cisco
!
no aaa new-model
memory-size iomem 25
!
ip cef
!
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 20.0.0.1
!
crypto ipsec transform-set TS-IPSEC esp-3des esp-sha-hmac
!
crypto map MAP-IPSEC 1 ipsec-isakmp
set peer 20.0.0.1
set transform-set TS-IPSEC
match address 100
!
interface Tunnel0
ip address 192.168.1.2 255.255.255.0
tunnel source 20.0.0.2
tunnel destination 20.0.0.1
crypto map MAP-IPSEC
!
interface Ethernet0
ip address 172.17.0.1 255.255.0.0
half-duplex
no keepalive
!
interface FastEthernet0
ip address 20.0.0.2 255.0.0.0
speed auto
crypto map MAP-IPSEC
!
router ospf 1
log-adjacency-changes
network 172.17.0.0 0.0.255.255 area 0
network 192.168.1.0 0.0.0.255 area 0
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
access-list 100 permit gre host 20.0.0.2 host 20.0.0.1
!
control-plane
!
line con 0
line aux 0
line vty 0 4
password cisco
login
!
end
次の「VPN(GREトンネルとルーティングプロトコル 4)」では、この設定を検証していきます。
