Telnetとは
Telnet(telecommunication Network)は、TCP/IPネットワークにおいて、機種依存しない仮想キャラクタ端末を定義してリモートのコンピュータを遠隔操作する場合に利用する機能です。
Telnetのおける操作は、CUIベースになります。コマンドプロンプト(シェル)から相手のマシンに遠隔でログインしてコマンドを実行します。
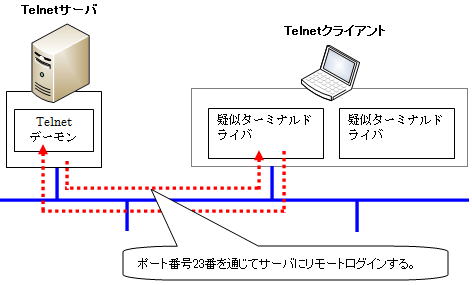
もともとTelnetは、数十年前、まだコンピュータが非常に高価だった時代、1台の高性能なホストコンピュータに廉価で低機能なキャラクタ端末(ダム端末)をたくさん配置してシリアルポートを通じてホストコンピュータにログインして使用するスタイルで利用されていました。
当時としては、なくてはならないプロトコルでしたが、現在、使用しなくなったわけではありません。
現在においては、WindowsベースのGUIに慣れており、Telnetは貧弱に思えるかもしれません。しかし、その分、接続の確立や制御も単純なので、軽快に接続することができます。
そのため、手軽にネットワーク上のサーバやネットワーク機器を遠隔操作する場合に重宝することから利用価値が高く一般的によく利用されています。
また、Telnetは、FTPと同様に、OSのコードの違いを吸収する異機種間接続をサポートしており、ウェルノウンポートとしてTCPの23番を使用しています。
セキュリティが弱いTelnet
上の「Telnetとは」では、Telnetは手軽にネットワーク上のサーバやネットワーク機器を遠隔操作する場合に手軽で重宝すると説明しました。
しかし、Telnetの利便性とセキュリティの危険性は表裏一体になっています。
Telnetの機能はWindowsベースのGUIに慣れていると一見、貧弱に感じてしまうかもしれませんが、ログインしてしまえば、ローカルマシンで行える操作をほとんど実行することができます。
コンピュータを理解している人にとっては、いろいろ操作が行えることは非常に便利ですが、ログインする人が悪意を持った第三者であったならどうでしょうか?
保存されている情報が漏洩したり、破壊されるなど様々な被害に発展してしまう危険があります。
と言うことは、インターネット経由のアクセス、社内ネットワーク経由のアクセスにおいてもTelnetの制限を可能な限り行うことが望ましいことになります。可能な限りTelnetサービスを行わないようにするべきです。
また、Telnetはログインの際の認証情報や認証成功後の通信内容も平文でやり取りするという問題があります。この問題もセキュリティの観点からは望ましいとは言えません。
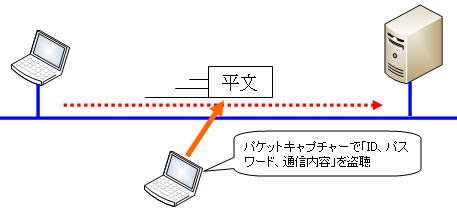
パケットが盗聴されると通信内容や認証情報などが漏洩し、様々な被害に発展してしまいかねません。
Telnetよりも、SSHなど暗号化したログイン方法の方が望ましく、こちらでの運用を考慮したり、ルーターなどリモートログインの手段がTelnetのみに限定される場合には、リモートログインしなくても済むような運用を考える必要があります。
