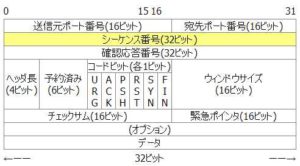
Port numbers that should be blocked by filtering
Port numbers that should be blocked by filtering
Here, we will explain dangerous ports that should be blocked by firewall filtering and why.
Block private IP addresses
A typical attack method is to spoof an IP address (IP spoofing). It is also used to prevent the source from being identified when infected with a virus, used as a stepping stone, or when conducting DoS or DDoS attacks.
At that time, the IP address that is often spoofed is a private IP address. this. A private address is an address that can only be used in a private and closed network such as a LAN.
Packets with this private IP address will never flow over the Internet. Filtering is generally defined to block packets with private IP addresses.
Block ICMP
By blocking ICMP packets so that they do not respond to Ping commands that use ICMP, the existence of internal computers and network devices can be hidden from the outside (Internet).
In other words, when viewed from the outside, since there is no response to the Ping command, the presence of computers and network devices cannot be confirmed, increasing security.
There is also a method of blocking all ICMP packets by setting the filtering, but there are cases where it is not easy to use. This is because there are cases where you want to use Ping from inside the firewall from the viewpoint of operation and maintenance.
At that time, ICMP messages are filtered to allow ICMP echo requests (type 8) that go out from inside the firewall and ICMP echo replies (type 0) that come in from outside the firewall. settings.
However, some routers have settings that block ICMP by default. Then you have to customize it.
Block Telnet
Allowing unlimited Telnet increases the risk of internal computers and network devices being hijacked by malicious individuals.
If it is hijacked, the settings will be changed as the attacker thinks. In that case, information will be stolen, and it will be used as a stepping stone to launch attacks on other sites and encourage nuisance. Therefore, settings must be made to block unnecessary Telnet connections.
Also, we must not forget the existence of applications other than Telnet that can perform remote operations. Be careful when using applications that can remotely control remote computers, such as Symantec’s pcAnywhere.
Block exploitable Windows ports with a firewall
It is safe to block TCP/UDP ports 135, 137, 138, 139, and 445 used by Windows with a firewall.
Windows is a popular target for malicious attackers because it is used by many users. There are many port numbers, but among them there is a port number that is often targeted.
It is the port used by viruses and worms that exploit security holes in Windows. In particular, TCP/UDP135 port numbers 137, 138, 139, and 445 are targeted as security holes.
The most famous is the Blaster worm, which caused a lot of damage in August 2003. It exploits a security hole called MS03-026 (RPC Interface Buffer Overrun Allows Code Execution).
Even if there is only one computer infected with the Blaster worm in the network, the network will be overloaded, the router will be overloaded and stuck, the bandwidth will be occupied, etc. Ignore the impact on the network It was impossible.
Unfortunately, even though the Blaster worm’s infectivity was tremendously eradicated, other computers were already infected at that time, and its infectivity threatened many network administrators.
Dangerous port numbers 137 and 138
Port numbers 137 and 138 are well known as chatty ports. For example, if you inquire about the connection status to port 137 of Windows, the following information can be obtained.
- computer name
- Domain name
- local logon name
- MAC address
- Is it a file server?
- Are you a master browser?
- Is it a domain controller
Such
If such information becomes known to attackers, it becomes easy prey.
So where are these port numbers 137 and 138 used?
It is used in the name resolution function of “NetBIOS over TCP/IP” (NBT) used in Windows networks.
This “NetBIOS over TCP/IP Thanks to
”NetBIOS over TCP/IP” may seem like a convenient protocol, but you should be aware that your computer itself is spreading information about itself without you even realizing it. It means that there is no need to send the information handled by “NetBIOS over TCP/IP” to the outside. Public servers are especially dangerous.
It is advisable to block these port numbers with a firewall. However, if you are using the Microsoft network in an intranet environment, a problem arises.
The point is that the convenience of the Microsoft network between each base will be lost. In that case, either give up the convenience of the Microsoft network, or, although it is not recommended, configure your firewall filtering to allow packets with these port numbers to pass.
By the way, to stop the NetBIOS service, press the “Advanced” button from the TCP/IP properties and select “Disable NetBIOS over TCP/IP” on the “WINS” tab. Port numbers 137, 138, Port 139 is closed.
Dangerous port numbers 139 and 445
Computers connected to the Microsoft network use a protocol called SMB (Server Massage Block) for communication such as file sharing and printer sharing.
SMB uses port numbers 139 and 445. In SMB communication, first, the IP address of the other party is obtained using the name resolution mechanism of NetBIOS.
A session is established by requesting the start of communication and permitting it by the other party. This is used to send user name and password information to the other party for authentication. If the authentication succeeds, you will be able to access the other party’s shared files.
Points to note when closing 135,137 to 139,445
If the router blocks packets with these port numbers, the convenience of the Microsoft network will be lost.
When sharing files in an intranet environment, sharing files by computer name and using printers are restricted.
In particular, blocking TCP/UDP 135 may make Active Directory unusable, so be careful.