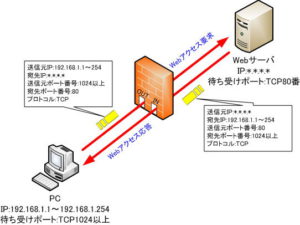
Information required for stateful inspection filtering
stateful inspection
Here, we will explain a technique called stateful inspection that strictly specifies return packets. This technique also looks deep inside the TCP header.
A TCP header is constructed as follows:
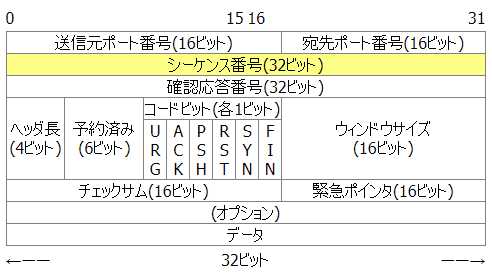
In TCP communication, we look at the “ACK” in the code bit section to determine whether to pass or block, and also check the sequence number.
This sequence number is the number needed to reassemble the received packet. Since packets may not arrive at the other party in the order in which they were sent, TCP uses this number to sort the packets.
A firewall that implements stateful inspection looks at the sequence number of passing packets, predicts the sequence number of the next returning packet, and discards packets received that differ from the predicted number. .
There are various types of firewalls that implement the stateful inspection function, from those that only check this sequence number to those that check even the data part in the packet.
Information required for filtering
To set up a firewall, we need to define a filtering table. At this time, it is not possible to define filtering conditions without understanding how applications communicate, the flow of communication procedures, and their characteristics.
In short, defining firewall filtering requires understanding application-specific communications.
Understanding TCP/UDP port numbers
Many applications use TCP or UDP as the transport layer protocol for communication.
First, you also need to know whether your application communicates using TCP or UDP, and what port number it uses.
The main TCP/UDP port numbers are shown in the table below.
● TCP well-known port
| port number | Service name | explanation |
| 20 | ftp-data | File Transfer [Default Data] |
| twenty one | FTP | File Transfer [Default Data] |
| twenty two | ssh | SSH Remote Login Protocol |
| twenty three | telnet | Telnet |
| twenty five | smtp | Simple Mail Transfer |
| 53 | domain | Domain Name Server |
| 67 | bootps | Bootstrap Protocol Server |
| 68 | bootpc | Bootstrap Protocol Client |
| 70 | gopher | Gopher |
| 79 | finger | finger |
| 80 | www-http | World Wide Web HTTP |
| 88 | kerberos | Kerberos |
| 110 | pop3 | Post Office Protocol – Version 3 |
| 119 | nntp | Network News Transfer Protocol |
| one two three | ntp | Network Time Protocol |
| 137 | netbios-ns | NETBIOS Name Service |
| 138 | netbios-dgm | NETBIOS Datagram Service |
| 139 | netbios-ssn | NETBIOS Session Service |
| 161 | snmp | SNMP |
| 162 | snmp trap | SNMP TRAP |
| 179 | bgp | Border Gateway Protocol |
| 443 | https | http protocol over TLS/SSL |
| 445 | microsoft-ds | Microsoft-DS |
| 636 | ldaps | ldap protocol over TLS/SSL |
Well-known port of UDP
| port number | Service name | explanation |
| 53 | domain | Domain Name Server |
| 67 | bootps | Bootstrap Protocol Server |
| 68 | bootpc | Bootstrap Protocol Client |
| 69 | tftp | Trivial File Transfer |
| 88 | kerberos | Kerberos |
| one two three | ntp | Network Time Protocol |
| 137 | netbios-ns | NETBIOS Name Service |
| 138 | netbios-dgm | NETBIOS Datagram Service |
| 139 | netbios-ssn | NETBIOS Session Service |
| 161 | snmp | SNMP |
| 162 | snmp trap | SNMP TRAP |
| 213 | ipx | IPX |
| 445 | microsoft-ds | Microsoft-DS |
| 520 | router | RIP |
| 546 | dhcpv6-client | DHCPv6 Client |
| 547 | dhcpv6-server | DHCPv6 Server |
Understand how the TCP three-way handshake works
In TCP, communication is performed by synchronizing with a mechanism called three-way handshake. Specifically, this is done by exchanging packets consisting of a SYN (synchronization control bit) and an initial sequence number in the following procedure.
| procedure | content |
| Step 1 | The sender sends a “SYN packet” to the other party. |
| Step 2 | The other party that receives the SYN packet sends a “SYN, ACK packet” to allow the connection to the sender. |
| Step 3 | The sender that receives the SYN ACK packet sends an ACK packet indicating connection initiation and initiates communication with the receiver. |
When specifying filtering conditions, you can specify whether to check for “ACK” or “SYN”.
Understand application-specific communication
For specifying general filtering conditions, you can specify filtering conditions by specifying source and destination IP addresses and port numbers, or create conditions to check the status of the TCP three-way handshake. increase.
However, some applications also have protocols that perform complex communications.
For example FTP.
FTP communication has the following characteristics.
・Two TCP connections are used for control and data transfer.
・On the server side, TCP port number 21 is used for control and TCP port number 20 is used for data transfer.
・First, establish a control connection from the client side.
– The server side establishes a connection for data transfer.
In this way, FTP performs complicated communication.
In the firewall settings, we will set the conditions to allow this complicated connection to pass without blocking it.
Notes on filtering
Understanding and defining application-specific communications is critical to specifying firewall filtering criteria. This is because application communication will not be established if the packets necessary for establishing a connection are blocked.