Difference Between Static and Dynamic Filtering
Difference between static and dynamic filtering
Here, we will explain the difference between static filtering and dynamic filtering.
For example, let’s see how the contents of the filtering table are defined for static filtering and dynamic filtering when a firewall that performs filtering is placed between a PC on the LAN side and a web server.
The inside of the firewall is the segment where the PC exists, and the outside is the segment where the web server exists.
For static filtering
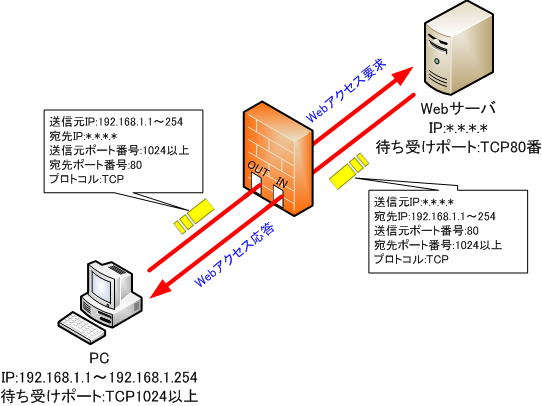
Register the packet forwarding and returning conditions in the filtering table so that only the packets that access the web server are passed.
The contents of the filtering table are as follows.
● Filtering table
| number | direction | protocol | source IP address | Destination IP address | source port number | destination port number | process |
| ① | → (inside → outside) | TCP | 192.168.1.* | *.*.*.* | * | 80 | passage |
| ② | ← (outside → inside) | TCP | * | 192.168.1.* | 80 | * | passage |
| ③ | * | * | * | * | * | * | cut off |
It is not known in advance which internal PCs will connect to which external web servers.
Therefore, in condition (2), since it is not known which internal PC communicates with which external web server, the IP address of the source web server is “*.*.*.*” and the destination IP address is “192.168 .1.*” and specify all internal PCs as destinations.
Also, since it is not possible to predict which port number the internal PC will use for communication with the destination port number, it is necessary to specify all port numbers (port numbers of 1024 or higher).
In this way, with static filtering, it is necessary to specify a fairly wide range and open a hole in the firewall, which increases the risk of allowing unexpected packets to pass.
For dynamic filtering
Dynamic filtering is basically the same as static filtering. Based on the conditions defined in the filtering table, it decides whether to pass the packet or block it.
Then, what is different from static filtering? In the case of dynamic filtering, the difference is that the filtering conditions change dynamically.
Dynamic filtering adds conditions to the filtering table to pass packets as needed and removes them when they are no longer needed.
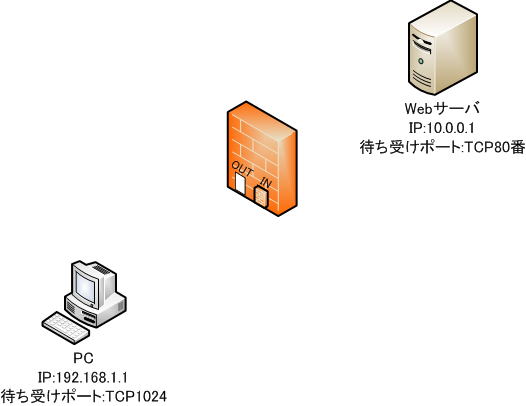
Now let’s see how the filtering table changes.
1. Filtering table before starting communication
Before starting communication, define the conditions in the filtering table to allow only web access from the inside.
● Filtering table
| number | direction | protocol | source IP address | Destination IP address | source port number | destination port number | process |
| ① | → (inside → outside) | TCP | 192.168.1.* | *.*.*.* | * | 80 | passage |
| ② | * | * | * | * | * | * | cut off |
At this time, the hole from the outside to the inside is still closed.
2. Filtering table at the start of communication
When an internal PC initiates communication to the web server, the firewall detects access to the web server. This is because it matches the pre-defined conditions for passing communication from the internal PC to the Web server. This condition will trigger a condition to be added to the filtering table for returning packets.
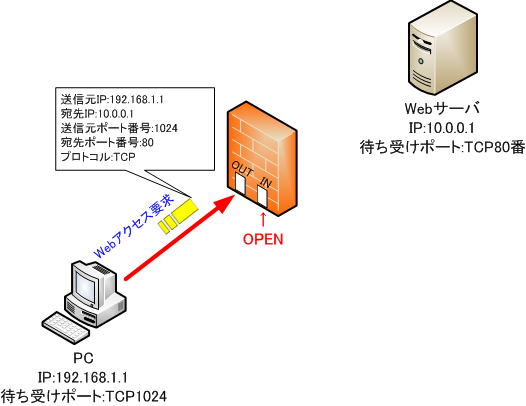
● Filtering table
| number | direction | protocol | source IP address | Destination IP address | source port number | destination port number | process |
| ① | → (inside → outside) | TCP | 192.168.1.* | *.*.*.* | * | 80 | passage |
| Add ⇒② | ← (outside → inside) | TCP | 10.0.0.1 | 192.168.1.1 | 80 | 1024 | passage |
| ③ | * | * | * | * | * | * | cut off |
At this time, I would like you to pay attention to the additional conditions. Conditions created by dynamic filtering are stricter than conditions defined by static filtering.
The source IP address is “10.0.0.1”, the destination IP address is “192.168.1.1”, and the destination port number is “1024”, which is stricter than the static filtering conditions. .
In this way, with dynamic filtering, conditions are created dynamically, so the hole in the firewall is pinpointed and smaller, reducing the risk of allowing unexpected packets to pass.
3. Filtering table during communication
Communication from the web server passes through the firewall because it matches the added condition (2).
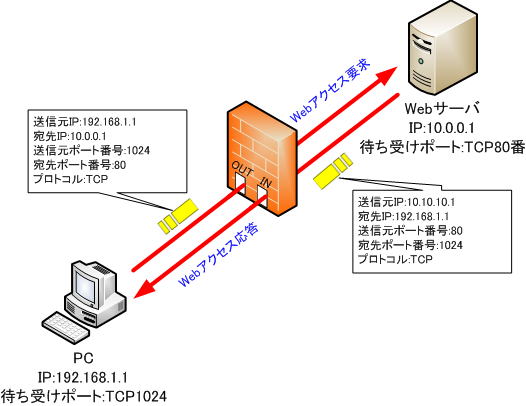
● Filtering table
| number | direction | protocol | source IP address | Destination IP address | source port number | destination port number | process |
| ① | → (inside → outside) | TCP | 192.168.1.* | *.*.*.* | * | 80 | passage |
| ② | ← (outside → inside) | TCP | 10.0.0.1 | 192.168.1.1 | 80 | 1024 | passage |
| ③ | * | * | * | * | * | * | cut off |
4. End of communication
When there is no communication from the web server, condition 2 is deleted to close the hole from the outer web server to the inner PC.
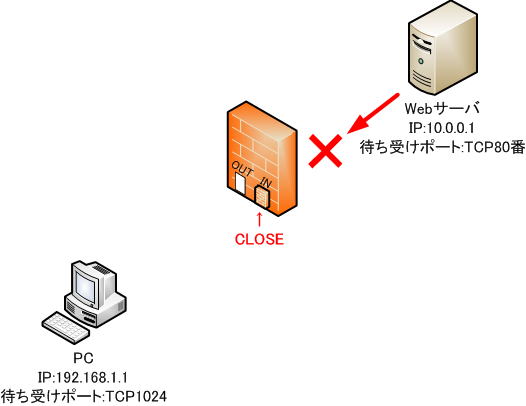
● Filtering table
| number | direction | protocol | source IP address | Destination IP address | source port number | destination port number | process |
| ① | → (inside → outside) | TCP | 192.168.1.* | *.*.*.* | * | 80 | passage |
| Delete② | |||||||
| ③ | * | * | * | * | * | * | cut off |
In this way, with dynamic filtering, the holes in the firewall need to be pinpointed and small, and the holes are opened and closed as needed, reducing the risk of allowing unexpected packets to pass.
So far, we have discussed the advantages of dynamic filtering, but there are also disadvantages.
Since the hole through which the packet passes is made dynamically with pinpoint accuracy, if the types of communication and the number of internal terminals increase, the number of conditions to be added dynamically will increase and the filtering table will become large. Therefore, managing the filtering table and checking the conditions will be burdensome.