What is MIME? E-mail encryption and electronic signature
What is MIME

Although e-mail is now a service that everyone uses, e-mail itself has a long history, dating back to the early days of the Internet.
Since the system was originally born in the English-speaking world, it is assumed that it will be used in English. Therefore, even now, all emails cannot be exchanged unless they are all text.
The character code used in e-mail is the ASCII code, which is the character set system used in the English-speaking world. ASCII code is also called 7-bit code because it uses only the lower 7 bits within the 8 bits.
If only ASCII code can be used, why is it possible to send emails with attachments such as Japanese text, spreadsheets, photos, etc.?
This is because there is a mechanism called MIME. Since the appearance of the mechanism called MIME, it has become possible to handle Japanese and binary data in e-mail. MIME is an abbreviation for “Multipurpose Internet Mail Extension” and is an extension standard that allows you to handle various formats in e-mail.
The following are mainly decided.
(1) Handling of sending and receiving binary data such as audio and images
(2) Support for international characters including handling of double-byte characters such as Asian countries
SMTP can only process e-mail as 7-bit text data, so data such as binary files cannot be sent as is.
So, MIME does the following:
(1) Encode (convert) the binary data part into text code on the sender’s mailer.
②Send an email as part of a text email.
(3) Decode (restore) to the original binary data at the mailer on the receiving side.
By doing so, even if it contains binary data, it can be treated as if it were text data.
MIME encoding uses encoding schemes such as Base64.
Internet is vulnerable
There are always risks associated with using the Internet.
- Eavesdropping
- Spoofing
- Tampering
The Internet is a huge network used by an unspecified number of people. If there are many people who use it, there are also many people who do bad things.
I think it’s easier to understand if you think about it in the real world. Almost every day, news and newspapers report violent crimes such as murder, robbery, and theft.
Not all people who connect to the Internet are healthy users. Speaking of bad things on the Internet, they are “eavesdropping”, “spoofing” and “falsification”.
If you connect to the Internet, you have the advantage of being able to communicate with terminals all over the world that are connected to the Internet, but conversely, it means that people around the world can see it.
To begin with, the Internet is an open network whose purpose is to publish information. Since it was created on the premise that it can be seen by everyone, it has the aspect of being vulnerable to security.
We must not forget that these three risks are latent when using the Internet.
◆ Eavesdropping
The data you communicate can be viewed by someone. The Internet is an open world. Unless encrypted, the data to be communicated is basically plaintext. Communication packets may be intercepted and viewed by malicious users.
◆Spoofing
Impersonation is when a third party pretends to be the real person and acts on the network.
If you are impersonated by another person, you may receive e-mails pretending to be from a different sender, read the content, post on bulletin boards using your name without permission, or use online shopping without permission. I will be shopping for
◆ Tampering
Falsification is the act of rewriting information without the permission of the administrator. Email content can be rewritten, HP content can be rewritten, and server logs can be rewritten to hide evidence of unauthorized intrusion.
E-mail encryption and electronic signature
As explained in “The Internet is vulnerable to security” above, the Internet is an open network whose purpose is to disclose information, so it is vulnerable to security.
E-mail delivered via the Internet is no exception, and threats of “eavesdropping”, “spoofing”, and “falsification” are always present. To avoid this risk and safely exchange e-mails, you can take the following actions.
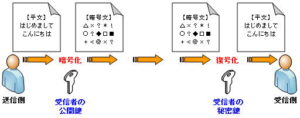
◆ Dealing with “eavesdropping” by encryption
If you want to see the contents of the email, just encrypt the message. That way, even if it’s eavesdropped, the contents of the original message won’t be revealed. The higher the encryption strength, the lower the risk that the original contents can be easily analyzed.
◆ Dealing with “spoofing” by attaching an electronic signature
Even if it is a paper contract, if it is affixed with a seal and a certificate of seal impression, the authenticity of the contract can be proved. By adding an electronic signature to e-mails, it is possible to deal with “spoofing”, in which the sender is disguised. This is because the author of the e-mail can be identified if it is electronically signed.
◆ Dealing with “tampering” by adding an electronic signature and encrypting
Once encrypted, the original message cannot be read. If you can’t read it, it’s difficult to rewrite it in context.
Furthermore, with an electronic signature, the sender cannot be disguised. In addition, the electronic signature contains a message digest created from the main body of the e-mail. You will know whether it has been tampered with.
This message digest is designed so that if the body of the email changes even a little, the message digest will also change, so if it has been tampered with, it can be detected.
◆S/MIME and PGP
S/MIME (Secure/Multipurpose Internet Mail Extensions) and PGP (Pretty Good Privacy) are commonly used for email encryption and electronic signatures. These two have encryption and signature functions, and this function is achieved by combining symmetric key cryptography, public key cryptography, and message digest functions.