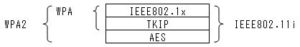
Wireless LAN encryption standards (WEP, TKIP, AES)
Wireless LAN encryption standard (WEP, TKIP, AES)
Wireless LAN Encryption Standard (WEP)
This is an early wireless LAN encryption standard implemented in many wireless LAN devices. Send data in encrypted form instead of plain text.
RC4 is used for the encryption algorithm. However, as an encryption method, its vulnerability has been pointed out, and cracking software such as AirSnort is on the market, so caution is required when using it.
The image of wireless LAN encryption by WEP is shown in the figure below.
Based on the WEP key shared by each AP and the IV (Initialization Vector) automatically generated by the system, pseudo-random numbers created using RC4 are used as keystorms to generate plaintext data. Encrypt plaintext data by XORing.
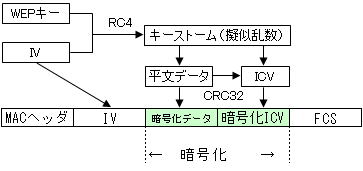
There are three WEP key sizes: 40-bit, 104-bit, and 128-bit, and the larger the size, the stronger the encryption. The encryption key (encryption key) length is the sum of the WEP key and IV, and is sometimes expressed as 64 bits, 128 bits, or 156 bits.
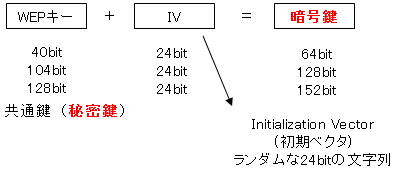
The WEP key can be a character string with the length shown in the table below.
| WEP key | Single-byte alphanumeric characters | Hexadecimal |
| 40 bits | 5 characters | 10 characters from 0 to 9 and A to F |
| 104 bits | 13 characters | 26 characters from 0 to 9 and A to F |
| 128 bits | 16 characters | 32 characters from 0 to 9 and A to F |
Problems with WEP
WEP has the following problems.
- WEP encryption does not encrypt the MAC address part.
- MAC address spoofing is easy.
- WEP cannot detect tampering.
- IV is 24bit and short.
Since the IV is 24 bits, only 2 24 (approximately 16.78 million) types of values can be used, so the same IV will circulate in a network with a large amount of traffic.
If the WEP key and IV are the same, the same keystorm can be generated, so if packets are captured for a certain period of time, plaintext data may be guessed.
Wireless LAN encryption standard (TKIP)
The TKIP method doubles the IV to 48 bits, which used to be a problem due to the same IV circulating on a network with a large amount of WEP traffic, and greatly improves the difficulty of decryption.
By extending the random number sequence (IV) that generates the encryption key (encryption key) to 48 bits, it is difficult to decipher even after collecting packets for several weeks to several months.
TKIP uses the same encryption algorithm as WEP, RC4. Even access points that support only WEP may be able to upgrade existing WEP-compatible devices to products that support TKIP by upgrading the firmware. In that case, since it is software processing, the processing speed will decrease.
TKIP complicates the encryption key generation procedure to make it difficult to decipher. The image of wireless LAN encryption by TKIP is shown in the figure below.
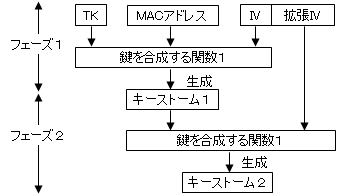
TKIP uses a 128-bit temporary key TK (Temporal Key), IV, and client MAC address to generate encryption keys. The ephemeral key length is 128bit and is changed every 10,000 packets. Also, the MAC address of the client is used, so every client will have a different key.
●Phase 1
Mix the MAC address and IV based on the temporary key.
●Phase 2
Mix the expanded part of the IV into Keystorm 1 to generate Keystorm 2.
In this way, by performing the key mixing process twice, even though it uses the same encryption algorithm (RC4) as WEP, it achieves higher security.
In addition, TKIP adds a field called MIC after the data part to detect message tampering.
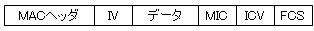
Wireless LAN encryption standard (AES)
AES is a strong encryption method adopted by the US government, reviewing the RC4 encryption algorithm, which was one of the causes of WEP vulnerability, strengthening the encryption algorithm itself, making it even more difficult to decipher. are doing
AES is based on the US government’s open call for strong cryptographic algorithms to replace the DES and 3DES that had been used up to that point in the late 1990s. Adopted.
AES has three key lengths of 128/192/256 bits, and its encryption strength is significantly stronger than that of DES.
Since AES is processed by hardware, there is no reduction in processing speed, but old wireless terminals and some wireless devices cannot handle it.
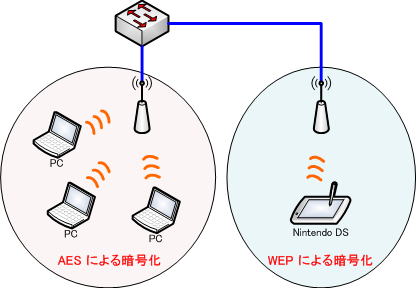
For example, if even one terminal that can only use WEP joins the wireless LAN network, the encryption of the entire network must be dropped to WEP encryption.
This is the case, for example, if you have an older device that only supports WEP, or if you want your Nintendo DS to join a WiFi network.
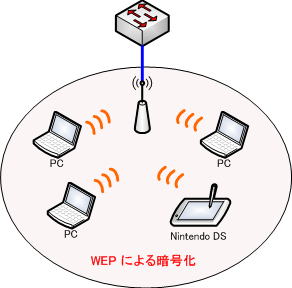
Not being able to use AES etc. in the entire wireless LAN network results in lower security, which is not a favorable situation. In this case, it is necessary to build a wireless LAN together with other security measures such as MAC address filtering.
Also, as shown in the figure below, it is effective to add an access point and divide the network into a WEP network and an AES network to build a wireless network.