Peer-to-Peer and Client-Server
How peer-to-peer works
Simply explaining whether it is a peer-to-peer network or a client-server network depends on whether or not a server is placed in the network.
A peer-to-peer network is a method in which no server is placed in the network.
This peer-to-peer type is suitable for networks with a small number of computers, such as SOHO and small offices.
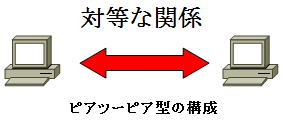
In the peer-to-peer type, all computers communicate equally. A network has a service provider and a service receiver.
In this method, the role is not fixed, but depending on the situation, one is the provider of the service and the other is the recipient of the service.
The network can be used easily, but with this method, operation management becomes difficult as the scale of the network increases. Network usage increases and security management becomes complicated.
In particular, as the number of users increases, it becomes difficult to manage the security basics of “which users are permitted which resources and which resources are not permitted.”
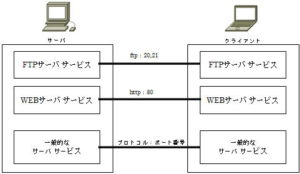
Client-server mechanism
Looking at a part of a large-scale and complicated network, it basically consists of communication between two computers (devices).
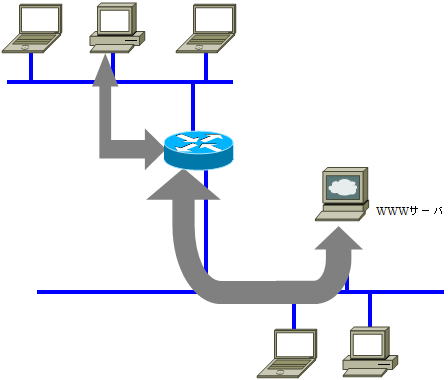
Normally, applications on one of the computers are waiting in a state of being activated so that communication can be performed at any time. An application on the other computer calls an application that has been started in advance, and the called side returns a response to communicate.
This method is called the client-server type, and many network service programs operate in this method. In the client-server model, the service provider and receiver are fixed, and their roles are clarified.
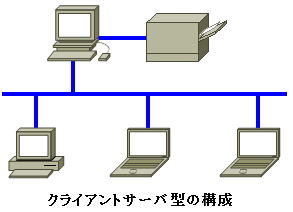
This format allows for centralized management of user accounts. An important part of security management is “which users are allowed which resources and which resources are not allowed”.
As the number of users increases, this management becomes complicated, but this centralized management method makes management easier. This method is useful when you have a large network and want to centrally manage security management, file management, printer sharing, and e-mail management.